 by Righard Zwienenberg Senior Research Fellow
by Righard Zwienenberg Senior Research Fellow
Phishers always try to find new ways to bypass security features and trick ‘educated’ users. Over the years we have seen simplistic phishing attempts where the required information had to be typed into the e-mail body. This worked at that time because phishing was new and hardly anyone had a notion of the implications. Later, when spam filters became aware of these kinds of mails, we saw the evolution to direct links in e-mail, then to obfuscated links in e-mail where the e-mails looked professional and had the appearance of official messages from the organization the phishers desire your information from.
One thing stayed the same and that is the language used in the phishing mails. Most often they are not correct in either a contextual way or grammar-wise. Regardless, all these attempts sooner or later will be blocked by spam filters or by the anti-malware products, or by URL reputation schemes such as Google’s Safe Browsing or Microsoft’s Smart Screen. But, too often, some people still fall victim for these phishers. One observation as to why this happens will be described later in this blog.
In the last few weeks, a new approach can be added to the portfolio of phishing attempts. The e-mail is accompanied by an attachment with the extension “htm” or “html”.
Now why would the phishers use an attachment with html-code rather than a link? There are several reasons for this. Amongst others:
- Executing the html-code locally will not have your browser go to a website and thus the URL reputation filter will not be applied.
- Executing the html-code locally for the browser means it is loaded from an intranet rather than from the Internet. Settings are usually less strict for files started/loaded from an intranet.
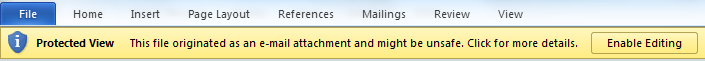
Some applications have a protection mechanism in place when specific files are executed or loaded directly as an attachment as, for example, Microsoft Office 2010, which will only load the file in a Protected View where active content is disabled
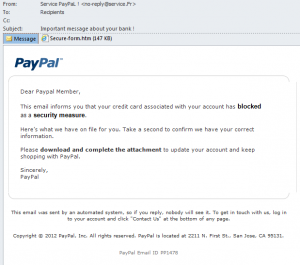
If we look at this specific phishing attempt, besides the fact that the window is not really a properly delineated window with a border, the grammar is far from perfect. Also ‘PayPal’ is addressing the recipient as “Dear Paypal Member” where the real PayPal (and other legitimate financial organizations – at least, those with a clue) will always address their customers by name and/or some other unique identifier known to both the provider and the customer. Also interesting is that this e-mail supposedly is coming from PayPal France, but the message is in English.
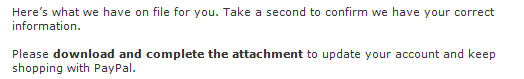
It implies that they already have information and they want to confirm it. Just double-clicking on the attachment will result in a warning.

We have already started to see e-mails where the reader is instructed to save the e-mail to the local system first, often to the Desktop for convenience, and then to execute or load them from there. But when the files are executed or loaded from the local system, the last safety-net provided by the mail program is bypassed.
With this phishing attempt we will see the page, presumably with the information they claim they already have and want to verify.
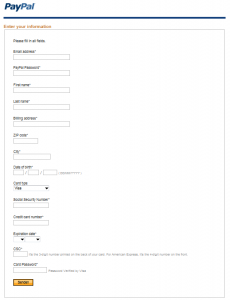
Interestingly they seem not to have any information from their customer yet.
Also noteworthy is the button to submit the information. Where the e-mail supposedly came from PayPal France, and the text and information is all in English, the submit-button has the text in German.
When the information is submitted, the form will contact a website where the information is retrieved using a php-script. When that is finished, the user will be forwarded to PayPal’s American homepage , resulting in a rather interesting collection of different languages in this phishing attempt.
So why do people still fall for phishing attempts? Education is the answer! Most people are completely new to the topic. If we limit ourselves to phishing for bank information, we know that more and more people move towards banking-online. Either for convenience, or driven by the fees the banks charge to bank in the old way, or because their bank has stopped allowing traditional banking methods. Lots of older people suddenly need to go online to do their banking and are unaware of these phishing attempts, and so fall for them.
It would be a good thing for banks to generate solid documentation on what a bank will NEVER ask for by e-mail, on their website, by telephone or any other means. It is in the banks’ own interest to educate their new online customers, as we expect that in 2012 we will see more and more of these phishing attempts.
ESET researchers have generated quite a few documents on phishing, and while some of them have been around for a while, the basic principles and advice on how to spot phishing emails still hold.
 by Righard Zwienenberg Senior Research Fellow
Phishers always try to find new ways to bypass security features and trick ‘educated’ users. Over the years we have seen simplistic phishing attempts where the required information had to be typed into the e-mail body. This worked at that time because phishing was new and hardly anyone had a notion of the implications. Later, when spam filters became aware of these kinds of mails, we saw the evolution to direct links in e-mail, then to obfuscated links in e-mail where the e-mails looked professional and had the appearance of official messages from the organization the phishers desire your information from.
One thing stayed the same and that is the language used in the phishing mails. Most often they are not correct in either a contextual way or grammar-wise. Regardless, all these attempts sooner or later will be blocked by spam filters or by the anti-malware products, or by URL reputation schemes such as Google’s Safe Browsing or Microsoft’s Smart Screen. But, too often, some people still fall victim for these phishers. One observation as to why this happens will be described later in this blog.
In the last few weeks, a new approach can be added to the portfolio of phishing attempts. The e-mail is accompanied by an attachment with the extension “htm” or “html”.
by Righard Zwienenberg Senior Research Fellow
Phishers always try to find new ways to bypass security features and trick ‘educated’ users. Over the years we have seen simplistic phishing attempts where the required information had to be typed into the e-mail body. This worked at that time because phishing was new and hardly anyone had a notion of the implications. Later, when spam filters became aware of these kinds of mails, we saw the evolution to direct links in e-mail, then to obfuscated links in e-mail where the e-mails looked professional and had the appearance of official messages from the organization the phishers desire your information from.
One thing stayed the same and that is the language used in the phishing mails. Most often they are not correct in either a contextual way or grammar-wise. Regardless, all these attempts sooner or later will be blocked by spam filters or by the anti-malware products, or by URL reputation schemes such as Google’s Safe Browsing or Microsoft’s Smart Screen. But, too often, some people still fall victim for these phishers. One observation as to why this happens will be described later in this blog.
In the last few weeks, a new approach can be added to the portfolio of phishing attempts. The e-mail is accompanied by an attachment with the extension “htm” or “html”.
 Now why would the phishers use an attachment with html-code rather than a link? There are several reasons for this. Amongst others:
Now why would the phishers use an attachment with html-code rather than a link? There are several reasons for this. Amongst others:
 If we look at this specific phishing attempt, besides the fact that the window is not really a properly delineated window with a border, the grammar is far from perfect. Also ‘PayPal’ is addressing the recipient as “Dear Paypal Member” where the real PayPal (and other legitimate financial organizations – at least, those with a clue) will always address their customers by name and/or some other unique identifier known to both the provider and the customer. Also interesting is that this e-mail supposedly is coming from PayPal France, but the message is in English.
If we look at this specific phishing attempt, besides the fact that the window is not really a properly delineated window with a border, the grammar is far from perfect. Also ‘PayPal’ is addressing the recipient as “Dear Paypal Member” where the real PayPal (and other legitimate financial organizations – at least, those with a clue) will always address their customers by name and/or some other unique identifier known to both the provider and the customer. Also interesting is that this e-mail supposedly is coming from PayPal France, but the message is in English.
 It implies that they already have information and they want to confirm it. Just double-clicking on the attachment will result in a warning.
It implies that they already have information and they want to confirm it. Just double-clicking on the attachment will result in a warning.
 We have already started to see e-mails where the reader is instructed to save the e-mail to the local system first, often to the Desktop for convenience, and then to execute or load them from there. But when the files are executed or loaded from the local system, the last safety-net provided by the mail program is bypassed.
With this phishing attempt we will see the page, presumably with the information they claim they already have and want to verify.
We have already started to see e-mails where the reader is instructed to save the e-mail to the local system first, often to the Desktop for convenience, and then to execute or load them from there. But when the files are executed or loaded from the local system, the last safety-net provided by the mail program is bypassed.
With this phishing attempt we will see the page, presumably with the information they claim they already have and want to verify.
 Interestingly they seem not to have any information from their customer yet.
Also noteworthy is the button to submit the information. Where the e-mail supposedly came from PayPal France, and the text and information is all in English, the submit-button has the text in German.
Interestingly they seem not to have any information from their customer yet.
Also noteworthy is the button to submit the information. Where the e-mail supposedly came from PayPal France, and the text and information is all in English, the submit-button has the text in German.
